Software
Computer Software
Finding the right software for your business does not have to be difficult. Contact us today and we will provide you with the best software for your needs. We work with leading software brands with reputable and reliable solutions.
Software Brands We Work With

Onboard Now
Customize the framework to match your small business processes using simple drag-and-drop tools.

For businesses →
Acronis Cyber Protect gives you the peace of mind to know your business is covered, with zero-day malware and ransomware protection, backup and forensic investigations.
Acronis Cyber Protect Cloud keeps our client’s data protected, with security, backup, disaster recovery, automation and management seamlessly integrated in one simple platform.

Ransomware protection

Patch management for businesses

Anti-malware for corporate environments
Work collaboration protection

IT disaster recovery

File backup and recovery

Data loss prevention (DLP)
Secure your business against modern cyber threats.
Data isn’t just another resource — it’s integral to your daily operations. Acronis’ cyber protection solutions safeguard you against data loss, security breaches, operational downtime, and the financial and reputational harm associated with each.








Microsoft 365
Microsoft 365 is our cloud-powered productivity platform. With a subscription to Microsoft 365, you can get: The latest productivity apps, such as Microsoft Teams, Word, Excel, PowerPoint, Outlook, OneDrive, and so much more. The ability to install on PCs, Macs, tablets, and phones.
What is the main function of Office 365? Office 365 lets you log in and connect to your office anywhere. Microsoft Office 365 is completely cloud-based, meaning you can access your files, email and Office programmes on your mobile, laptop or desktop wherever you like

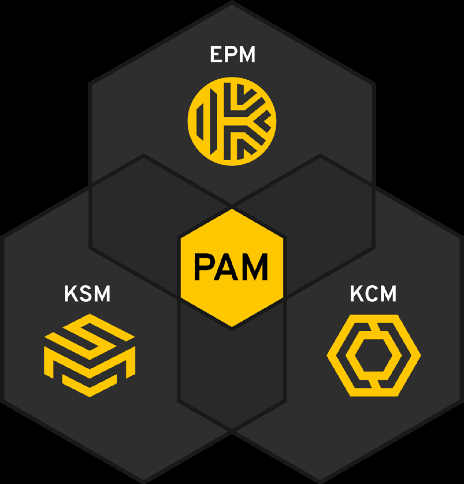
Keeper – The next-gen, zero-trust and zero-knowledge privileged access management (PAM) solution.
KeeperPAMTM was created to fully protect perimeterless and multi-cloud environments with just the features you need.
KeeperPAM
Keeper’s patented PAM platform enables organizations to achieve complete visibility, security, control and reporting across every user on every device in any organization. The platform is cloud-based, enables zero-trust and zero-knowledge security and meets compliance mandates by unifying three integral solutions into one unified solution.
82% of breaches involve the human element – with the majority due to stolen or weak passwords, credentials and secrets
PASSWORD MANAGER
Enables organizations to securely manage, protect, discover, share and rotate passwords with full control and visibility to simplify auditing and compliance.
SECRETES MANAGER
Delivers a fully-managed, cloud-based solution to secure infrastructure secrets such as API keys, database credentials, access keys and certificates
CONNECTION MANAGEMENT
Provides an agentless remote desktop gateway for instant privileged session management, remote infrastructure access and secure remote database access to RDP, SSH keys, database and Kubernetes endpoints – no VPN required.

Black Fog
Black Fog’s data privacy features decrease the risks associated with data loss and data breaches from external attacks and insider threats associated with the loss of customer data. On device data privacy
- Mitigate the risk of data loss through geofencing
- Minimize data collection on every endpoint
- Prevent unauthorized data collection and profiling
- Ensure customer data stays on the device
- Protect your employees wherever they are On device data Security
- Prevent data loss using behavioral analytics
- Reduce the surface area exposed to attackers
- Access detailed reporting and analysis of threat vectors
- Lower the cost of compliance
- Detect network anomalies through data exfiltration Enterprise Console
- BlackFog Enterprise consists of endpoint agents and the Enterprise cloud console, used to centrally manage and view all threats and events generated at the endpoint.
- The console provides insights into the origin of threats with a consolidated view across all departments, while each department receives access to a threat dashboard for their business unit.
- Monitor each department and filter events and devices in the master view.
- Global settings and cloning provide rapid on-boarding.
- Analytics provide detailed impact assessments across all your networks and devices
WHY BlackFog for POPI?
- Prevents cyberattacks across all endpoints
- Prevents data breaches, data loss and insider threats
- Blocks the unauthorized collection and transmission of customer data from every device on and off the network
- Monitors data exfiltration in real time to ensure no unauthorized data leaves the network
- Prevents ransomware, malware, spyware and phishing
- On device privacy protection ensures your corporate and customer data is secure
- Detailed compliance reporting for regulators and information officers
- Mitigates reputational damage and improves customer trust
- Platforms:
- Windows 7+
- MacOS 10.11.5+
- iOS 10.3+
- Android 5.0+

Beachhead: THE EMAIL ENCRYPTION APP
PURPOSE OF THE EMAIL ENCRYPTION APP
Data Subjects want their Personal Information (PI) and sensitive data to be secured and protected, including when it is emailed. All password-encrypted PDF file(s) are created using AES 256-bit encryption prior to sending, ensuring the app employs strong security to satisfy even the strictest auditor or regulation. Software to secure any outgoing emails.
As powerful or simple as you need it!
Do the right thing for your business by taking real and effective) steps to safeguard personal/sensitive information, including when it is emailed. Using this app to send emails as encrypted will make your business look professional to stakeholders and will demonstrate that you are serious about information security and sensitive data handling, even to auditors and regulators
Send Securely
Data Subjects want their Personal Information (PI) and sensitive data to be secured and protected, including when it is emailed. All password encrypted PDF file(s) are created using AES 256-bit encryption prior to sending, ensuring the app employs strong security to satisfy even the strictest auditor or regulation.
Earn Trust
Do the right thing for your business by taking real and effective) steps to safeguard personal/sensitive information, including when it is emailed.
Using this app to send email as encrypted will make your business look professional to stakeholders and will demonstrate that you are serious about information security and sensitive data handling, even to auditors and regulators
Secure Outgoing Email Without Hassle
Tightly integrated with the Outlook email client on Windows PC makes for effortless and hassle-free encrypted email sending using the renowned PDF standard which means there are no keys, certificates or special decryption software needed by the recipient(s) – just a password and a PDF viewer like Acrobat Reader which is widely used and totally free.
Remain Compliant
Laws require your business to provide proper protection and safeguarding of all personal and/or sensitive data, including when it is emailed.
The app boasts some outstanding features and functions making it a total breeze for your business to implement and for employees to use(immediately). This software will yield an instant return on investment (ROI) for your business.
Bank-Grade Email Encryption
- A simple and intuitive app installed as an add-in for Microsoft Outlook on any Windows PC to send emails as encrypted, in a way that is easy for the sender and simple for the recipient, using the PDF standard.
- Encrypt the full message body and attachments, or encrypt attachments-only either in their native format (for editing), or have it automatically converted to PDF.
- You can send the actual password or a password-hint instead.
- Passwords can be automatically generated for Recipients or it can be manually assigned using custom passwords.
- Importantly, this app provides for a personal password list as well as the use of a shared “organization-wide” (admin-controlled) password list.

SMBsecure™️
Patented technology, deployed in minutes, makes securing your organisational data on Windows and Mobiles a total breeze!
ENCRYPT
SAFEGUARD
PROTECT
DEFEND
All-in-One Fully Managed Service to De-risk your Business with Data & Email Encryption, Device Lock/Wipe, Phishing Simulations, Cyber Risk Training, Reporting and Proof of Data Encryption.
Data-on-Device Encryption
Make use of encryption methods native to your operating system to ensure the most seamless and most secure means of encryption for your data at rest on your PC & Mobile Device. On Windows PCs, you get persistent Bitlocker for Volume level encryption, as well as fully managed key control, backup & retrieval with realtime encryption risk monitoring for your convenience.
Outlook Email Encryption
When sending email containing any personal or sensitive data from Microsoft Outlook on your PC, as the Sender you are the “Responsible Party” so send it using secure end-to-end encryption in password-protected portable document format (PDF), just like the banks do! The Outlook plugin allows flexible options to send data securely to avoid 3rd party data exposure, earn trust from customers & stakeholders by demonstrating effective security, and remain compliant with the Protection of
Personal Information Act (POPIA), VAT Act, and other requirements which require safe custody of consumer/customer data.
Device Lock/Wipe
- Kill device immediately if stolen,
- Quarantine data access until correct access can be confirmed,
- Fully managed cloud initiated controls.
Phishing Simulations & Security Awareness Training
- Secure your first line of defence, the Human Layer,
- Be prepared by learning to identify phishing scams which mimic real-life attack,
- Automatic training so you don’t fall prey to scams designed to steal your (or your customers’) information and money,
- Improve your Human Firewall with breach prevention techniques and strategies,
- Fully managed so you don’t have to do anything
- Become AWARE to Avoid Being a Victim.
SMBsecure™️ provides valueadded Protection for Small and Medium Businesses.
Now you can build and maintain trust, compliance, and competitive
advantage!
GFI KerioControl
KerioControl is a next-generation firewall and unified threat management product for small and medium-sized businesses (SMBs) that are looking for a comprehensive solution for their security needs.
Protect your network from viruses, malware and malicious activity with Kerio Control. This easy-to-administer security solution includes a next-generation firewall and router, intrusion detection and prevention (IPS), gateway antivirus, VPN, and web content and application filtering. These comprehensive capabilities, with unmatched deployment flexibility, make Kerio Control the ideal choice for small and mid-sized businesses.
Eliminate the risk and cost of connectivity or threat protection downtime with High availability/fail-over protection. With High availability, if a crash or failure occurs the second machine jumps into action immediately.
Protect network integrity through deep packet inspection, advanced routing, intrusion prevention and a high-performance VPN client.
Industry-leading web content and application filtering across 141 categories, plus the ability to view individual users’ internet activity through detailed reports.
Preserve the Integrity of Your Network
- High availability/ fail-over protection eliminates the risk and cost of connectivity or threat-protection downtime.
- Without High-availability, prime device failure due to a power surge or other cause often leads network administrators to put a simple router in place to reestablish connectivity.
- Protect your servers with deep packet inspection and advanced networking routing—including simultaneous support for IPv4 and IPv6.
- Create both in and outbound tra!c policies, restricting communication by specific URL, application, tra!c type, content category and even time of day
Improve Productivity with Industry-Leading Web, Content and Application Filtering
- Selectively block, allow or log access to 141 continuously updated categories of content and applications with the optional Kerio Control Web Filter w/ application awareness.
- View individual users’ Internet activity, refine tra!c-shaping rules and more with automatic, detailed reports from Kerio Control Statistics sent to your email inbox.
- Use insights from reporting to limit legal liability and improve productivity by blocking access to sites, applications and content categories or limiting it to specific time of day, users/user groups and user locations.
Administer Quickly and Easily—Anytime, Anywhere
- Manage Kerio Control from your desktop or remotely from a tablet device.
- Stay in control of all your Kerio deployments from anywhere using MyKerio. Manage multiple Kerio Control deployments through a free centralized web interface providing consolidated system information, automatic configuration backup, status monitoring, system notifications and complete remote configuration.

Trend Micro Antivirus+ Security provides essential online protection for 1 PC. Using Advanced Artificial Intelligence Learning technology, Antivirus+ Security shields you against spam, viruses, malware, spyware, and ransomware.
What is Trend Micro and how it works?
Trend Micro Inc.
The company develops enterprise security software for servers, containers, & cloud computing environments, networks, and end points. Its cloud and virtualization security products provide automated security for customers of VMware, Amazon AWS, Microsoft Azure, and Google Cloud Platform.



TOPIA analyses, prioritises and protects third-party apps against threats and attacks.
Manage your organisation’s security cycle from start to finish and protect more, faster by focusing on threats that matter most.

0-Day
TOPIA’s Zero-Day Analysis™ tool uses predictive analysis to track malware activity and predict incoming attacks. Now you can rest easy knowing you’ll never get caught off-guard

xTags™
xTags™ help prioritise threats using contextual scoring, like prioritisation parameters, access authority and activity status in order to determine the risk level of every application and asset in your organisation.

Patchless
Never think twice about deploying a patch again. TOPIA’s propriety Patchless Protection™ tool secures threats swiftly and safely by developing a protective force-field around high-risk, vulnerable apps.
Onboard Now
Customize the framework to match your small business processes using simple drag-and-drop tools.